45 aws security best practices
Security, Identity & Compliance | AWS Architecture Center Best Practices for Security, Identity, & Compliance Learn how to meet your security and compliance goals using AWS infrastructure and services. To learn current AWS recommendations and strategies to use when designing cloud architectures with security in mind, see the Security Pillar - AWS Well-Architected Framework. Learn best practices for securing your AWS account and resources It's a best practice to actively monitor your account and its resources to detect any unusual activity or access to your account. Consider one or more of the following solutions: Enable Amazon CloudWatch billing alerts to receive automated notifications when your bill exceeds thresholds you define. For more information, see Amazon CloudWatch FAQs.
Nine AWS Security Hub best practices | AWS Security Blog In this post, I'll provide nine best practices to help you use AWS Security Hub as effectively as possible. 1. Use the AWS Labs script to turn on Security Hub in all your AWS accounts in all regions and to establish your existing Amazon GuardDuty master/member hierarchy

Aws security best practices
GitHub - prowler-cloud/prowler: Prowler is an Open Source ... Prowler is an Open Source security tool to perform AWS security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness. It contains more than 240 controls covering CIS, PCI-DSS, ISO27001, GDPR, HIPAA, FFIEC, SOC2, AWS FTR, ENS and custom security frameworks. AWS VPC Security: 13 Best Practices [The 2022 Guide] - Hyperglance The best practice is to split your production, staging, and pre-production environments across different VPCs. Image courtesy of AWS 5. Use Security Groups To Control Resource Access It's vital that you factor in AWS Identity Access Management (IAM) when you're planning and setting up your VPC. What is AWS Security? Risks, Best Practices, and More Best Practices for AWS Security. In August 2016, Amazon released a 74-page document detailing the best practices for AWS users. Some of the biggest takeaways are: Think of security at every layer. Instead of using just one firewall to secure all of your virtual networks, be sure to use virtual firewalls on every network that you create.
Aws security best practices. 5 Best Practices for AWS NACLs (Network Access ... - DZone Sep 21, 2018 · This post looks at the top five best practices for AWS NACLs, including using it with security groups inside a VPC, keeping an eye on the DENY rule, and more. 5 Best Practices for AWS NACLs ... Top 10 security best practices for securing data in Amazon S3 Sep 02, 2021 · Security Hub collects security data from across AWS accounts, services, and supported third-party partner products and helps you analyze your security trends and identify the highest priority security issues. The AWS Foundational Security Best Practices standard is a set of controls that detect when your deployed accounts and resources deviate ... AWS Security Best Practices Amazon Web Services AWS Security Best Practices Page 1 Introduction Information security is of paramount importance to Amazon Web Services (AWS) customers. Security is a core functional requirement that protects mission- critical information from accidental or deliberate theft, leakage, integrity compromise, and deletion. AWS Security Best Practices | Classroom Training | AWS Students should have familiarity with AWS services and a strong background in information security concepts, techniques, and paradigms in the areas of networking, operating systems, data encryption, and operational controls. We recommend that attendees of this course have completed: AWS Security Fundamentals AWS Security Essentials Find a class
9 AWS Security Best Practices: Securing Your AWS Cloud But AWS best security practices aren't the only reason for this platform's popularity. Is AWS Cloud Secure? Amazon Web Services (AWS) is a comprehensive platform that has won universal acclaim ... Security best practices in AWS IoT Core - AWS IoT Core You can use AWS IoT Device Advisor to validate that your devices can reliably connect to AWS IoT Core and follow security best practices. IAM Policy Variables Amazon Cognito Identity AWS IoT Device Defender CloudWatch Logs for AWS IoT Keep your device's clock in sync It's important to have an accurate time on your device. Security - AWS Well-Architected Framework The Security pillar encompasses the ability to protect data, systems, and assets to take advantage of cloud technologies to improve your security. The security pillar provides an overview of design principles, best practices, and questions. You can find prescriptive guidance on implementation in the Security Pillar whitepaper. Topics 51 AWS Security Best Practices | McAfee Blog AWS infrastructure security best practices. 1) Familiarize yourself with AWS's shared responsibility model for security. Like most cloud providers, Amazon operates under a shared responsibility model. Amazon takes responsibility for the security of its infrastructure, and has made platform security a priority in order to protect customers ...
AWS Security Best Practices - CoreStack Learn the most important AWS Security Group best practices and follow step-by-step instructions and examples to configure them. Chapter 2 - S3 Security Learn the AWS S3 security principles of least privilege, access monitoring, encryption, and more, to protect against misconfiguration and data leakage. Chapter 3 - AWS NACL AWS Security Best Practices - AWS Security Best Practices AWS Security Best Practices. AWS Whitepaper. Welcome; AWS Documentation AWS Whitepapers AWS Whitepaper. AWS Security Best Practices. PDF RSS. Notice: This whitepaper has been archived. For the latest technical information on ... AWS Security Best Practices Checklist | CDW Some practices may be as easy as performing regular data backups or creating appropriate password policies but can go a long way in increasing overall security. By following this checklist, you can help ensure that your cloud-based and in-house services are as secure as possible: 1. Create Strong Password Policies Best Practices | AWS Security Blog The AWS Security team has made it easier for you to find information and guidance on best practices for your cloud architecture. We're pleased to share the Best Practices for Security, Identity, & Compliance webpage of the new AWS Architecture Center.
AWS Cloud Security Best Practices | CrowdStrike Guilherme (Gui) Alvarenga, is a Sr. Product Marketing Manager for the Cloud Security portfolio at CrowdStrike. He has over 15 years experience driving Cloud, SaaS, Network and ML solutions for companies such as Check Point, NEC and Cisco Systems. He graduated in Advertising and Marketing at the Universidade Paulista in Brazil, and pursued his ...
21 AWS Security Groups Best Practices | McAfee Blog As with any AWS service, it is crucial that AWS security groups are properly configured to protect against security risks and threats and best practices are followed: 1) VPC flow logging: Enable Virtual Private Cloud (VPC) flow logging. VPC flow logs provide visibility into network traffic that traverses the VPC and can be used to detect ...
Security best practices in IAM - AWS Identity and Access ... To help secure your AWS resources, follow these best practices for AWS Identity and Access Management (IAM) . Topics Require human users to use federation with an identity provider to access AWS using temporary credentials Require workloads to use temporary credentials with IAM roles to access AWS Require multi-factor authentication (MFA)
Best Practices - Security - Amazon Elastic Container Service Each topic in this guide starts with a brief overview, followed by a list of recommendations and best practices that you can use to secure your Amazon ECS clusters. Topics Shared responsibility model AWS Identity and Access Management Using IAM roles with Amazon ECS tasks Network security Secrets management
Security | ANSWERSDB.COM Programmatic access including API calls to AWS services should be performed using temporary and limited-privilege credentials such as those issued by the AWS Security Token Service. AWS provides resources that can help you with Identity and access management. To help learn best practices, explore our hands-on labs on managing credentials ...
9 AWS Security Best Practices - Alert Logic [ Data Security Best Practices] 6. Backup Your Data You never know if you're going to need to restore data after a breach, so back up your data regularly. You can do this by using AWS Backup. This app makes it easy to automate backups across your AWS environment, so you never have to worry about losing important information.
AWS Security Best Practices Checklist - DZone Security AWS Cloud Security Best Practices. Tuning Redshift. The Top Ten Cloud Tools From AWS. AWS security Database Redshift (theory) cluster AI Data (computing) Virtual private cloud application ...
Getting Started: Follow Security Best Practices as You Configure Your ... Following security best practices can help prevent your root account from being compromised, which is an important safeguard because your root account has access to all services and resources in your account. Create a strong password for your AWS resources
13 AWS Security Best Practices - Check Point Software By following this AWS security best practices checklist, it is possible to improve the security of an AWS deployment. Identify Security Requirements 1. Define and Categorize Assets in AWS: It is impossible to secure systems that you don't know exist.
AWS Cloud Security Best Practices: Securing AWS Environments - Rapid7 Having said that, if you understand the unique aspects of cloud security and apply best practices, AWS can be as secure as (or even more secure than) an on-premises network. The importance of strong AWS cloud security. Strong AWS security is important for the same reasons why cybersecurity in general is important.
Aws network acl vs security group best practices jobs Search for jobs related to Aws network acl vs security group best practices or hire on the world's largest freelancing marketplace with 21m+ jobs. It's free to sign up and bid on jobs.
AWS Foundational Security Best Practices standard The AWS Foundational Security Best Practices standard is a set of controls that detect when your deployed accounts and resources deviate from security best practices. The standard allows you to continuously evaluate all of your AWS accounts and workloads to quickly identify areas of deviation from best practices.
What is AWS Security? Risks, Best Practices, and More Best Practices for AWS Security. In August 2016, Amazon released a 74-page document detailing the best practices for AWS users. Some of the biggest takeaways are: Think of security at every layer. Instead of using just one firewall to secure all of your virtual networks, be sure to use virtual firewalls on every network that you create.
AWS VPC Security: 13 Best Practices [The 2022 Guide] - Hyperglance The best practice is to split your production, staging, and pre-production environments across different VPCs. Image courtesy of AWS 5. Use Security Groups To Control Resource Access It's vital that you factor in AWS Identity Access Management (IAM) when you're planning and setting up your VPC.
GitHub - prowler-cloud/prowler: Prowler is an Open Source ... Prowler is an Open Source security tool to perform AWS security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness. It contains more than 240 controls covering CIS, PCI-DSS, ISO27001, GDPR, HIPAA, FFIEC, SOC2, AWS FTR, ENS and custom security frameworks.
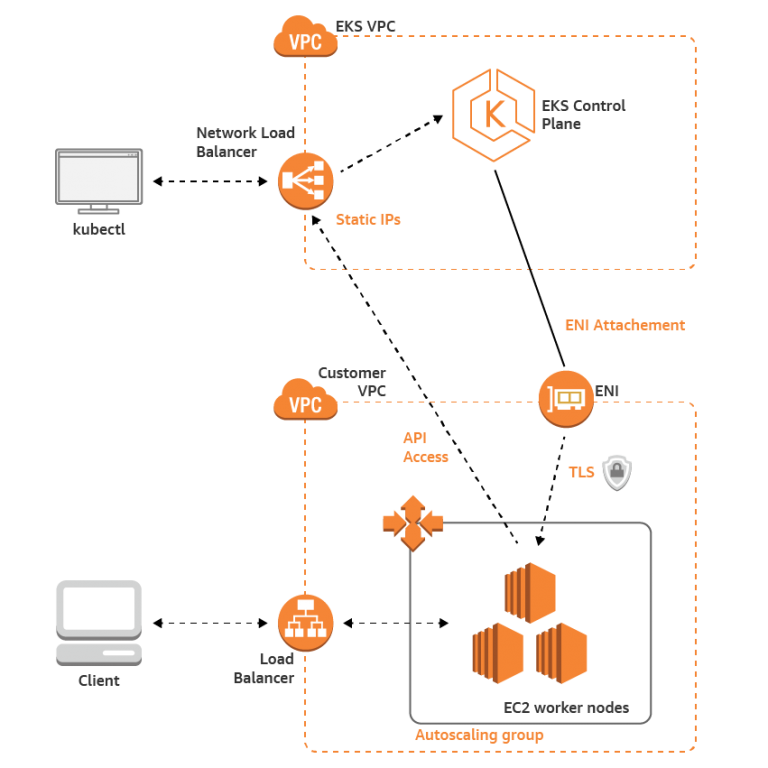



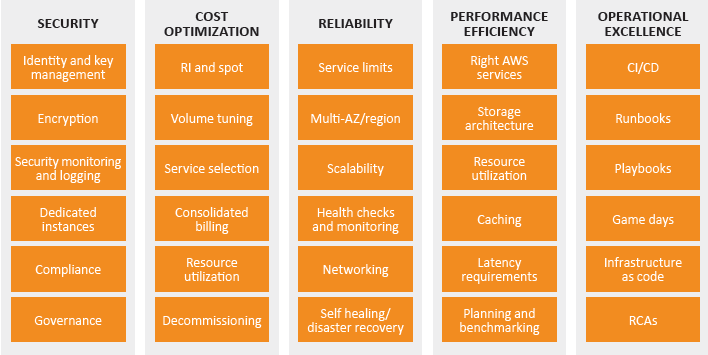

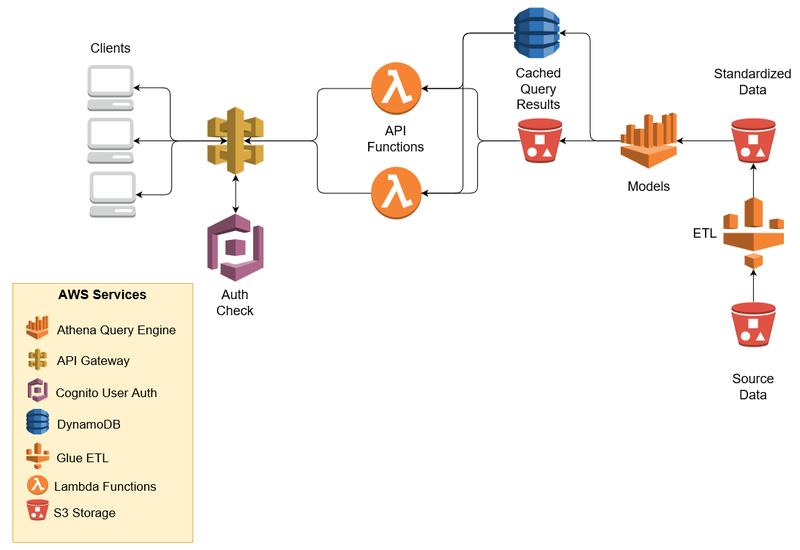








0 Response to "45 aws security best practices"
Post a Comment